Security is a basic human concept that has become more difficult to define and enforce in the modern age. In primitive societies, security was limited to ensuring the safety of the group’s members and protecting physical resources.
In a complex society like ours, the significance of sharing and securing important resources has increased. IT security is the process of implementing measures and systems designed to securely protect and safeguard information (data – business, personal including those not yet conceived) utilizing various forms of technology developed to create, store, use, and exchange such information against any unauthorized access, misuse, malfunction, destruction, or improper disclosure.

Some Of Our Security Services
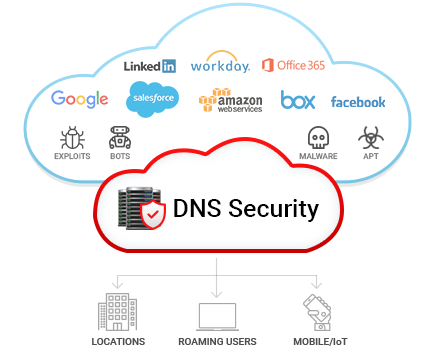
Defend against volumetric attacks, exploits, DNS hijacking, and DNS-based data exfiltration with unique behavioral analytics.
The DNS protocol can be exploited easily. It is easy to craft DNS queries that can cause the DNS server to crash or respond with a much-amplified response that can congest the bandwidth. The queries can be spoofed which means attackers can direct huge amounts of traffic to its victim with the help of unsuspecting accomplices (open resolvers on the internet).
Traditional protection like firewalls leave port 53 open and don’t do much in terms of preventing DNS attacks. All these reasons make the DNS an ideal attack target.
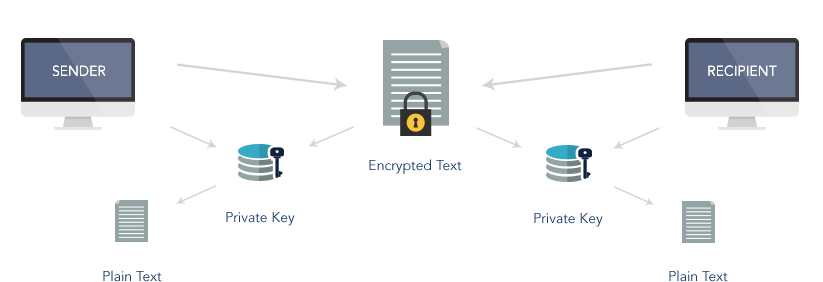
This is the process of encoding messages or information in such a way that only authorized parties can read it. To guard against advanced threats in a complex and evolving climate of virtualization, cloud services, and mobility, while maintaining regulatory compliance, organizations must increasingly take a data-centric approach to safeguarding their sensitive information.
The growth in digitizing information within certain industry sectors combined with an increased need for information security poses strong market demand for products that can securely enable wireless and wired networking and mobile communications, and email messaging.
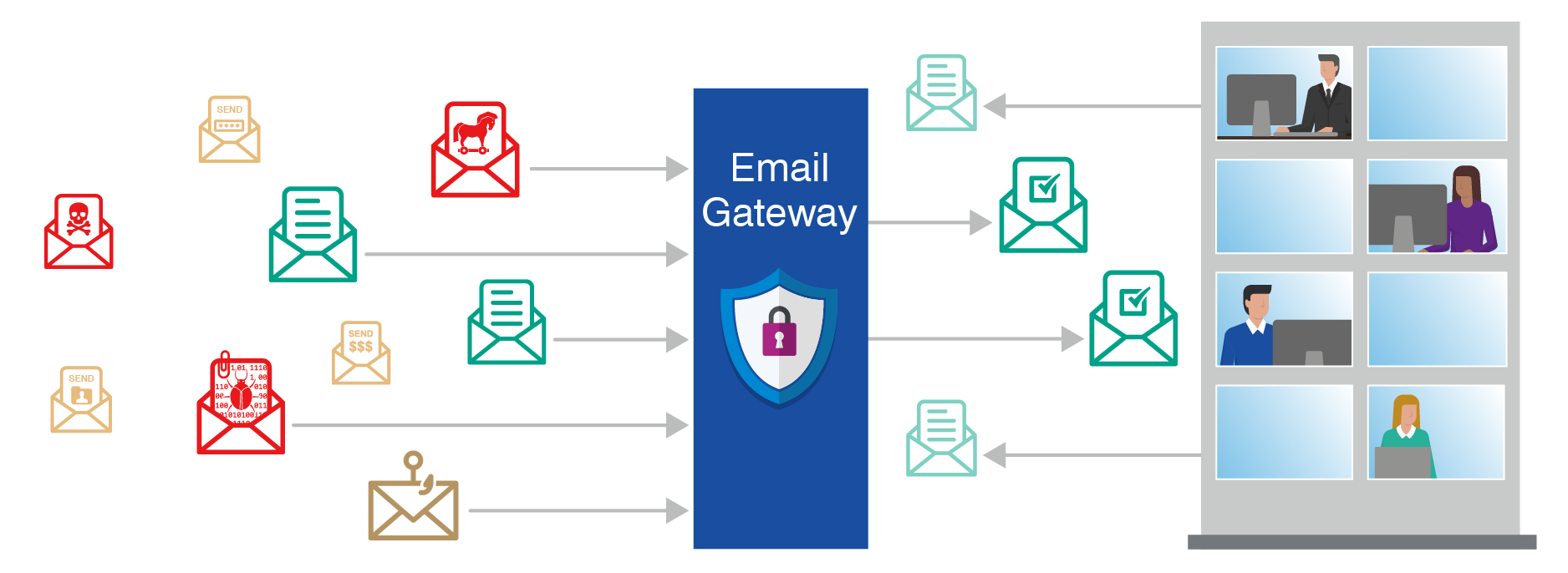
Endpoint/Email Security – refers to a methodology of protecting the corporate network when accessed via remote devices such as laptops or other wireless, mobile device, email encryption, data loss prevention, anti-malware, anti-botnets, and spam protection.
By encrypting and decrypting messages and attachments, secure email is as easy as regular email for both senders and recipients.
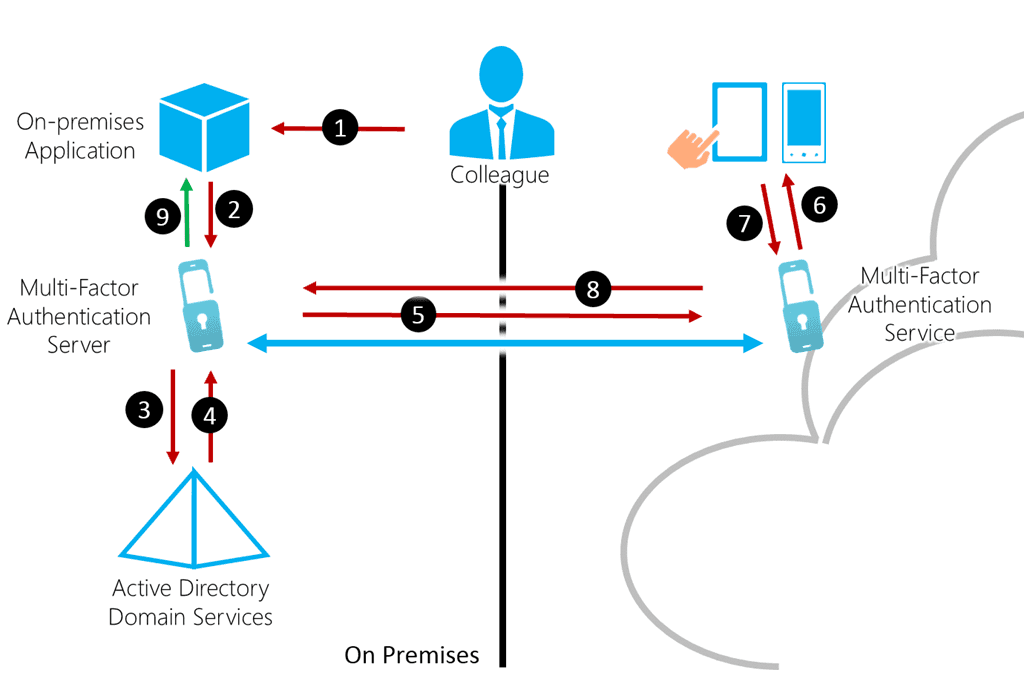
Multifactor Authentication – is a security system that requires more than one method of authentication from independent categories of credentials to verify the user’s identity for a login or other transaction.
Our platform allows you to enable multi-factor authentication and mix and match with other authentication methods to meet your policies so you can provide step-up authentication for specific resources and contexts. Create group and role-specific rules and authentication chains for sensitive data access. Collect identity attributes from multiple sources like external identity repositories.
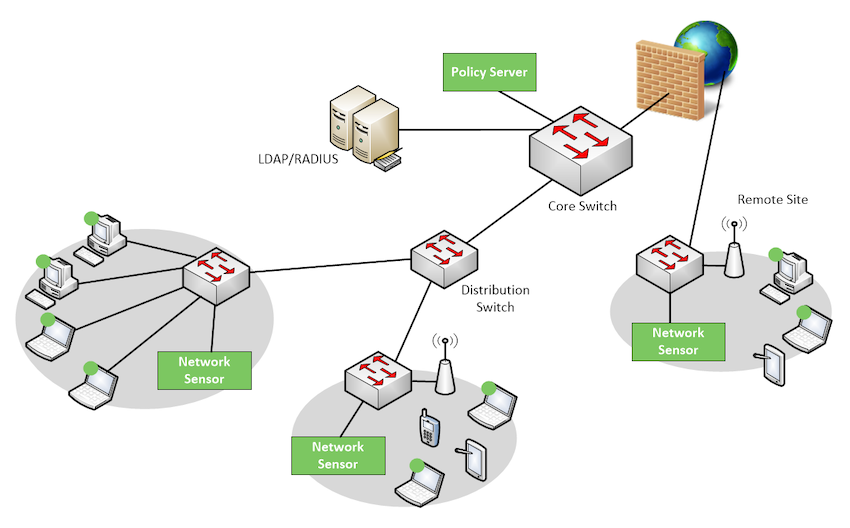
Network Access Control – also referred to as Network Admission Control. A traditional network server (NAS) is a server that performs authentication and authorization functions for potential users by verifying logon information. In addition to these functions, NAC restricts the data that each particular user can access, as well as implementing anti-threat applications such as firewalls, antivirus software and spyware detection programs. NAC also regulates and restricts the things individual can do once they are connected.
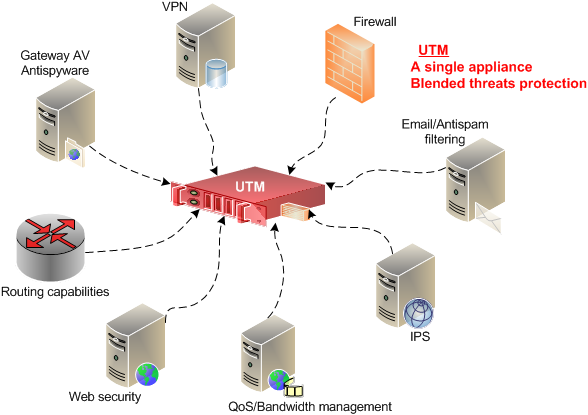
Unified Threat Management (UTM) Device – also referred to as next generation firewall (NGFW) are typically purchased as cloud services or network appliances to provide firewall, intrusion detection, antimalware, spam and content filtering and VPN capabilities in one integrated package that can be installed and updated easily
They also include more advanced features such as identity-based access control, load balancing, quality of service (QoS), intrusion prevention, SSL and SSH inspection and application awareness.